|
|

|
Story that got Stephen Glass caught is hilarious. Pre-internet was so easy
 Poast new message in this thread
Poast new message in this thread

Date: May 13th, 2025 6:35 PM Author: internet g0y Lol at this guy making up laws, conferences, companies. And he repeatedly did this over years.
Exposure
In the May 18, 1998, issue, The New Republic published a story by Glass (by then an associate editor) entitled "Hack Heaven", purportedly telling the story of a 15-year-old hacker who had penetrated a company's computer network, then been hired by that company as a security consultant. The article opened as follows,
Ian Restil, a 15-year-old computer hacker who looks like an even more adolescent version of Bill Gates, is throwing a tantrum. "I want more money. I want a Miata. I want a trip to Disney World. I want X-Men comic [book] number one. I want a lifetime subscription to Playboy – and throw in Penthouse. Show me the money! Show me the money! ..." Across the table, executives from a California software firm called Jukt Micronics are listening and trying ever so delicately to oblige. "Excuse me, sir," one of the suits says tentatively to the pimply teenager. "Excuse me. Pardon me for interrupting you, sir. We can arrange more money for you."[16]
Adam Penenberg, a reporter with Forbes magazine, endeavored to fact check the piece, in part to explain how "Forbes Digital had been scooped by a weekly political publication."[17] Beyond Glass's story, Penenberg found no search results for "Jukt Micronics", and, when he made an inquiry to the California Franchise Tax Board, the tax board reported back that no such company had ever paid taxes.[17] Penenberg also found that several other claims Glass made in the article appeared to be false: Glass claimed that law-enforcement officials in Nevada ran articles pleading with companies not to hire hackers, but Bob Harmon, Public Information Officer for the Nevada State Attorney General's Office, said no such ads ran.[17] Glass claimed that 21 states were considering a "Uniform Computer Security Act", which would "criminalize immunity deals between hackers and companies," but law enforcement officials and the National Conference of Commissions on Uniform State Laws were unaware of any such proposed legislation.[17] Glass claimed that there had been a computer-hacker conference in Bethesda, Maryland, sponsored by the "National Assembly of Hackers", but the Forbes team "could not unearth a single hacker who had even heard of this outfit, let alone attended the conference."[17]
On Friday, May 8, 1998, Forbes presented its full findings to Charles Lane, the lead editor of The New Republic.[18] Lane had, to that point, been unaware of potential issues with the article.[18] Lane had Glass take him to a Hyatt Regency Hotel in Bethesda, Maryland, where Glass had claimed the computer-hacker convention occurred.[12][4] He found that the hotel's layout did not match the story's description, the building in which the piece said the event took place had not been open on the supposed day of the conference, and the restaurant where the hackers supposedly had a dinner banquet afterwards closed in the mid afternoon.[12] Lane dialed a Palo Alto number provided by Glass and spoke with a man who identified himself as a Jukt executive; when he realized that the "executive" was actually Glass's brother, he fired Glass.[19] |


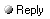
Date: May 13th, 2025 6:38 PM Author: ,.,..,.,..,.,.,.,..,.,.,,..,..,.,,..,.,,. lol @ boomers and x'ers falling for THIS:
HACK HEAVEN By Stephen Glass The New Republic
Ian Restil, a 15-year-old computer hacker who looks like an even more adolescent version of Bill Gates, is throwing a tantrum. "I want more money. I want a Miata. I want a trip to Disney World. I want X-Man comic book number one. I want a lifetime subscription to Playboy, and throw in Penthouse. Show me the money! Show me the money!" Over and over again, the boy, who is wearing a frayed Cal Ripken Jr. t-shirt, is shouting his demands. Across the table, executives from a California software firm called Jukt Micronics are listening - and trying ever so delicately to oblige. "Excuse me, sir," one of the suits says, tentatively, to the pimply teenager. "Excuse me. Pardon me for interrupting you, sir. We can arrange more money for you. Then, you can buy the comic book, and then, when you're of more, say, appropriate age, you can buy the car and pornographic magazines on your own."
It's pretty amazing that a 15-year-old could get a big-time software firm to grovel like that. What's more amazing, though, is how Ian got Jukt's attention - by breaking into its databases. In March, Restil - whose nom de plume is "Big Bad Bionic Boy" - used a computer at his high school library to hack into Jukt.
Once he got past the company's online security system, he posted every employee's salary on the company's website alongside more than a dozen pictures of naked women, each with the caption: "the big bad bionic boy has been here baby." After weeks of trying futilely to figure out how Ian cracked the security program, Jukt's engineers gave up. That's when the company came to Ian's Bethesda, Maryland, home - to hire him.
And Ian, clever boy that he is, had been expecting them. "The principal told us to hire a defense lawyer fast, because Ian was in deep trouble," says his mother, Jamie Restil. "Ian laughed and told us to get an agent. Our boy was definitely right." Ian says he knew that Jukt would determine it was cheaper to hire him - and pay him to fix their database - than it would be to have engineers do it. And he knew this because the same thing had happened to more than a dozen online friends.
Indeed, deals like Ian's are becoming common - so common, in fact, that hacker agents now advertise their commissions on websites. Computer Insider, a newsletter for hackers, estimates that about 900 recreational hackers were hired in the last four years by companies they once targeted. Ian's agent, whose business card is emblazoned with the slogan "super-agent to super-nerds," claims to represent nearly 300 of them, ages nine to 68.
A failed basketball agent, Joe Hiertgot into the industry when one of his son's friends, 21-year-old Ty Harris, broke into an Internet security firm three years ago and came to him for advice. The software maker paid Harris $1 million, a monster truck, and promised "free agency" - meaning he can quit and work for a competitor at any time.
Of course, a cynic might say hacker schemes look an awful lot like protection rackets. 'That's an awfully nice computer network you got there. It'd be a shame if somebody broke into it...' Law-enforcement officials, in particular, complain that deals between companies and their online predators have made prosecution of online security breaches impossible.
"We are basically paralyzed right now," explains Jim Ghort, who directs the Center for Interstate Online Investigations, a joint police project of 18 states. "We can't arrest or prosecute most hackers, because corporate victims are refusing to come forward. This is a huge problem."
In March, Nevada law-enforcement officials got so desperate they ran the following radio advertisement: "Would you hire a shoplifter to watch the cash register? Please don't deal with hackers." The state took to the airwaves shortly after a hacker broke into a regional department store's computer system and instructed it to credit his Visa card about $500 per day.
According to Nevada officials, the boy racked up more than $32,000 in credit before he was caught - but the store wouldn't press charges. It let him keep the money, then threw in a $1,500 shopping spree- - all in exchange for showing them how to improve their security.
Little wonder, then, that 21 states are now considering versions of something called the Uniform Computer Security Act, which would effectively criminalize immunity deals between hackers and companies - while imposing stiff penalties on the corporations who make such deals. "This is just like prostitution," says Julie Farthwork of the anti-hacker Computer Security Center, which helped draft the legislation. "As a society, we don't want people making a career out of something that's simply immoral."
Not surprisingly, hackers hate the proposed legislation. They see themselves as "freelance security investigators," and they even have their own group- - the National Assembly of Hackers - to lobby against the new law. " Really, hackers have to put in a lot of sunk costs before they find the one that's broken and get paid," says Frank Juliet, the group's president. "So, it's definitely a large community service that we are doing."
Less predictable, however, is the opposition of companies that have been hacked. It seems they don't like the proposed law, either, because they're worried they'll be stuck with no legal way to patch holes in their security systems. The Association of Internet-based Businesses has actually formed a task force with the National Assembly of Hackers to lobby against the law.
It remains to be seen who will win, but, until new laws are passed, hackers like Ian Restil will continue to enjoy a certain exalted status - particularly among their peers. At a conference sponsored by the National Assembly of Hackers last week, teenage hackers and graying corporate executives flocked to Ian, patting him on the back and giving him high-fives.
"We're so proud of him," said Ian's mother. "He's doing such good things, and he's so smart and kind." At the formal dinner that followed, the emcee explained that Ian had just signed a contract for $81,000 in scholarship money - and a collection of rare comic books. The audience applauded wildly. Then, Ian stood on his chair and took a bow. He announced that he had hacked into a new company and frozen their bank account temporarily. "And now they're going to show me the money," he said, swirling his hips and shaking his fists. "I want a Miata. I want a trip to Disney World...." |

Date: May 13th, 2025 7:04 PM Author: internet g0y (http://www.autoadmit.com/thread.php?thread_id=5724617&forum_id=2...id.#48928134) |


Date: May 13th, 2025 7:19 PM Author: ,.,..,.,..,.,.,.,..,.,.,,..,..,.,,..,.,,. i think we looked up some of glass's other articles a while ago. he used to write for slate.com. one of his pieces from 1997 was called something like "amazon.con," and his thesis was that amazon sucked and would probably fail. (http://www.autoadmit.com/thread.php?thread_id=5724617&forum_id=2...id.#48928159) |


Date: May 13th, 2025 8:40 PM Author: .,.,....,.,.,.,:,,:,....,:::,....,:,.,.:...,:.::, I think an investigation found that half of his articles were fabricated (http://www.autoadmit.com/thread.php?thread_id=5724617&forum_id=2...id.#48928325) |


Date: May 13th, 2025 10:45 PM Author: David Poaster Wallace https://slate.com/news-and-politics/1997/01/amazon-con.html
After calling the stores, we connected to Amazon using Netscape Navigator 3.0 and a 28,800-baud modem. Amazon has a special page dedicated to the Turow book, complete with a picture of the cover and some unenlightening amateur commentaries from other Amazon users. The psychology text, not surprisingly, was listed with no description and no commentaries. Amazon said it would take one to two weeks to order.
After clicking your purchases into a “shopping cart,” you are directed to a “secure Netscape server” that will encrypt your credit-card information. After this is done, you are told: “Finalizing Your Order Is Easy.” Nothing could be further from the truth. Lower down in the verbiage, Amazon concedes, “Though we have tried hard to make this form easy to use, we know that it can be quite confusing the first time.” Amazon users have to page through screen after screen of details about shipping charges, refund rules, and disclaimers about availability and pricing. Then you are told to allow between three and seven days for delivery after your book leaves Amazon’s warehouse. “Upgrading to Next Day Air does NOT [their emphasis] mean you’ll get your order the next day.”
Advertisement
Total online time from when we accessed Amazon’s home page to when we completed the book order: 37 minutes and 12 seconds. It would be shorter once you got the hang of it. |


Date: May 13th, 2025 8:37 PM Author: .,.,....,.,.,.,:,,:,....,:::,....,:,.,.:...,:.::, Boomers fell for it. His editor Michael Kelly was a boomer and would be nearly 70 today. He got exposed in 1998 and Gen X had zero power then . Some were still in high school. The only people reading New Republic back then were 30+. (http://www.autoadmit.com/thread.php?thread_id=5724617&forum_id=2...id.#48928312) |


Date: May 13th, 2025 7:23 PM Author: Cornel West (🧐) shouldve stuck to the piano (http://www.autoadmit.com/thread.php?thread_id=5724617&forum_id=2...id.#48928166) |


Date: May 13th, 2025 8:31 PM Author: DR. trillionaire (Ed.D., moon studies) Twist: this, published a day later, was real https://www.villagevoice.com/hackers-excellent-adventures/
Hackers’ Excellent Adventures by
WILLIAM BASTONE May 19, 1998
With his baby face and doughy body, 17-year-old Joshua Gilson does not look like your typical FBI quarry.
In fact, huddled over his Toshiba laptop, with rock music blaring from his bedroom stereo and Jerry Springer flickering on the TV, the Sheepshead Bay resident looks like any other teenager, albeit one experiencing maximum sensory overload, 1998-style.
But actually Gilson is part of a nationwide networkof teenage computer hackers who have stolen everything from Internet accounts to credit card numbers, a cybergang that has flourished despite a yearlong effort by the FBI to curb this online piracy, the Voice has learned. “I’ve stolen accounts and stuff like that. I didn’t even think it was that big of a deal,” Gilson said. “Everybody does it.”
For months, federal investigators have been serving subpoenas and search warrants at the homes of these young hackers, carting away computers, disks, modems, and other items as parents watch in horror. Agents with the FBI’s computer crimes squad have recently raided homes across the metropolitan area–from Brooklyn to the New Jersey suburbs–as part of a probe into wide-scale credit card fraud and other cybercrimes.
In several instances, agents visited the same residences more than once — first in mid 1997 and then again earlier this year — because some young hackers were undeterred by the federal probe. According to one court record, a hacker recently boasted to a friend that “nothing could be done to him because he was a minor.”
One federal investigator acknowledged that while “it’s tough to prosecute a juvenile,” the FBI is “not always sure you’re gonna find a teenager” at “the end of the string.” The source added, “And if you do, it still doesn’t mean the game is off, because if the damage is severe enough it is still a crime and it’s still a problem.”
Since the probe is ongoing–and every target appears to be underage — investigators have tried to keep details of the case confidential, including whether any teenagers have been arrested on federal charges. But interviews with several subjects of the criminal inquiry and a confidential FBI document obtained by the Voice provide a detailed look at the current investigation.
The federal probe began last spring, when agents learned of the “massive deployment of a password-stealing program” on the Internet, according to the FBI document. The scheme targeted accounts on America Online (AOL), the nation’s largest online service. AOL is a favorite nesting place for young hackers, who congregate in chat rooms with names like Dead End and Island 55. “Fifteen seems to be the preferred age for an AOL hacker,” said one long-in-the-tooth 18-year-old hacker.
Rich D’Amato, an AOL spokesman, said the service does not comment on specific criminal investigations, but that the company has a “working relationship” with law enforcement agencies “in an effort to combat cybercrime.” D’Amato added that AOL regularly warns its members about password- and credit-card-stealing programs, known online as “Trojan Horses.”
With these stolen passwords, teenagers illegally accessed the accounts of thousands of unsuspecting AOL customers as well as employees of the online giant, sources said. In some instances, hackers were able to access an AOL user’s credit information and order merchandise with the pilfered card number.
Along with password theft, many hackers developed or distributed a separate computer program that hijacked credit card numbers. Variations of that program, designed to look like an official communication from AOL, were e-mailed to thousands of account holders. When AOL customers opened the file, they would receive a message informing them of some type of billing discrepancy and that they needed to resubmit their credit card information. Though it appeared the information had been sent to AOL, carefully cloaked hackers were actually on the receiving end.
Armed with stolen credit card numbers, teenagers would use them to buy merchandise as well as open other Internet accounts. But a favorite prank of many hackers is to use the information for what is known as “carding.”
It seems that every young hacker is a member of a loosely knit online “crew” and within those predominantly male groups everybody has an enemy or two, rivalries formed during chat room sessions filled with insults and put-downs. When one Southern hacker learned that a reporter had met with one of his New York rivals, the teenager had only one question: “Is he fat?” When told that his foe was, in fact, a bit overweight, the teenager whooped, “I knew it!”
Because of these geographic considerations, crew members rarely meet in person to settle their differences. Instead, hackers prefer to “card” their rivals by ordering expensive merchandise with a stolen credit card and having it delivered to their foe’s home. Four teenagers told the Voice that they had been carded, though each denied ever pulling the prank himself.
Paul Lesiak, a 16-year-old known online as Pizza, said he has refused the delivery of a fax machine and dozens of roses sent to his New Jersey home. Bay Ridge’s Alex Berger, 15, also said he turned away flowers and a fax, as well as a refrigerator. Ian Massey, 18, of Louisville, Kentucky, said after a beef with a New Jersey hacker, the teenager “carded a 14-inch dildo to my house.” Joshua Gilson has seen flowers, a fax machine, a microwave oven, and a refrigerator arrive at his apartment door. Gilson, known as Ski, said the Panasonic fax–which he kept–came courtesy of an Illinois hacker with whom he was fighting. After the delivery, Gilson said his rival called him with the taunt, “Hey, Ski, did you like that fax machine?”
Lesiak told the Voice that twice in the last year FBI agents arrived at his Passaic County home to question him and seize computer equipment. While saying that “I didn’t mess with credit cards,” Lesiak admitted authoring a password-stealing program, which he circulated among other hackers. Prior to the FBI’s first visit, in mid 1997, Lesiak said that a friend told him of being questioned by agents. “I got all paranoid, so I killed most of the stuff off my computer,” said the high school sophomore. But when two weeks passed and the FBI had not contacted him, Lesiak said he restored some of the password- stealing programs.
Shortly after he reinstalled the incriminating programs, FBI agent Linda Walsh and a partner arrived at Lesiak’s door asking to examine his computer, a request with which the teen’s parents complied.
A month ago, Walsh returned to Lesiak’s home, this time with a subpoena for his computer equipment. Lesiak was not sure what the FBI was investigating him for this time, and he could not locate his copy of the subpoena (though during a phone interview he did try to locate the document, calling out matter-of-factlyto his mother, “Mom, do you have the subpoena from when the FBI was here?”).
While Lesiak admitted that his heart was in his throat when the agents first showed up at his house, the 16-year-old has gotten a bit bolder. He called Walsh’s FBI partner “a fat idiot. He’s like white trash times three. You’d expect him to have half a brain to be investigating this kind of stuff, but he had no idea what he was talking about.”
Berger also has had two FBI visits and claimed not to go online anymore because “I don’t wanna lose more computers.” The high school sophomore said agents found password stealers on his hard drive and he admitted that a “couple of times” he used stolen credit card numbers to buy merchandise for himself, though he termed that activity “nothing serious.” But by having the merchandise delivered to his home, Berger said, “that’s how I got caught.”
The most recent round of FBI searches in the New York area was apparently triggered by a late-February incident online in which tens of thousands of people nationwide–from Buffalo to Honolulu–received a death threat in their electronic mail.
The trouble started, oddly enough, when Ian Massey called Gilson a “poophead.”
The pair, along with Chris Bladis, a Summit, New Jersey, teen known as K1ng, were in a private chat room at 2 a.m. when they decided to have a three-way telephone conversation. During that talk, Massey and Gilson–both high school dropouts now studying for a GED–traded insults. “I called him a poophead,” Massey said, noting seriously that he used “the old-school insult . . . because people haven’t heard them in a long time and they don’t quite know how to respond.” Massey said he chose the childish term over “shithead” or “fuckface” because “I get called shithead every day.”
Sitting in his bedroom, Gilson responded by typing out a message that included Massey’s name, address, and home phone number and the threat, “I have your credit card number and all your personal information. Call me right now . . . if you don’t I will kill you and your family.” Gilson, using a stolen AOL account, said he immediately sent the e-mail to more than 1000 addresses.
Gilson said that over the next two days his pal Bladis sent the threatening message to tens of thousands of other e-mail addresses. Bladis’s father Richard said that while the 17-year-old has had his computer equipment seized by the FBI and been the subject of an investigation by U.S. postal inspectors, he doubted that his son was involved in circulating the death threat. The postal probe involved charges that the teenager used stolen credit cards to make purchases. As a result, the elder Bladis said, he was forced–on his son’s behalf–to make restitution totaling “a couple of thousand dollars” for these charges.
One of Bladis’s hacker buddies told the Voice that Bladis was a clearinghouse for stolen credit card numbers, once offering him a file of 16,000 numbers in exchange for some stolen AOL accounts.
After Gilson’s and Bladis’s handiwork, Massey said he was deluged with calls from people asking, “Why did you threaten to kill my family?” The 18-year-old contacted the Louisville FBI office and, within two days, agents executed a search warrant at Gilson’s Brooklyn home, looking for evidence of several federal crimes, including wire fraud and unauthorized access to a computer. During the March 1 raid, investigators seized the 17-year-old’s computer, monitor, two keyboards, and the Panasonic fax machine that was paid for with a stolen credit card.
“Now that I think about it, it was definitely stupid,” Gilson said of his spam (mass e-mail) attack.
Sitting in the apartment he shares with his mother, Gilson, who turned 17 in January, is dressed in a hooded Adidas sweatshirt, a Nike baseball cap, and Nike sneakers. He is wearing two silver hoops in his left ear, one in the lobe, one at the top of his ear. He looks sleepy and explains that he had been out with friends until four in the morning. Getting up for school was not a consideration, though, since he dropped out of the 10th grade last year.
His small bedroom, which looks out onto noisy Avenue U, is dominated by a large graffiti tag on the wall over his single bed. It reads “Ski,” his all-purpose vandalism handle.
The teenager recalled his first encounter with the FBI in early 1997, when agents questioned him about password-stealing programs and credit card fraud. Gilson said he was shocked when agent Walsh showed him a detailed paper trail of his illegal exploits on AOL. “It was sick,” he said. “It was like they’d been stalking me.” Gilson said agents wanted him to cooperate and keep a log of the names, addresses, and phone numbers of other hackers with whom he would subsequently be in contact. He promised to do that, but, Gilson admitted, “I never bothered.”
When agents searched his home in March, Gilson said that he was placed up against the living-room wall and frisked. Agents asked him no questions and left with all of his computer equipment, save two audio speakers. Within weeks, accompanied by a lawyer, he attended a meeting with FBI agents and prosecutor Marcia Isaacson of the major crimes unit of the Manhattan U.S. Attorney’s office. “I had to tell them everything that I knew,” said Gilson.
The teenager said he does not know what, if any, charges he will face. But he expects to make an appearance in federal court soon. “I don’t think they’re sending me to jail. Because, like, for this? I mean, murderers are in jail.” |


Date: May 13th, 2025 8:33 PM Author: DR. trillionaire (Ed.D., moon studies) if you used “tos” by “pizza”’to terminate people’s aol accounts in the 90s, this is the developer:
Lesiak admitted that his heart was in his throat when the agents first showed up at his house, the 16-year-old has gotten a bit bolder. He called Walsh’s FBI partner “a fat idiot. He’s like white trash times three. You’d expect him to have half a brain to be investigating this kind of stuff, but he had no idea what he was talking about.” |


Date: May 13th, 2025 8:35 PM Author: .,.,....,.,.,.,:,,:,....,:::,....,:,.,.:...,:.::, Like serial killers and other sociopaths, he got too bold (http://www.autoadmit.com/thread.php?thread_id=5724617&forum_id=2...id.#48928296) |


Date: May 13th, 2025 8:49 PM Author: Traditional Latin ass Luckily this jewish reporter was the only one to ever lie (http://www.autoadmit.com/thread.php?thread_id=5724617&forum_id=2...id.#48928360) |


Date: May 13th, 2025 10:48 PM Author: https://imgur.com/a/o2g8xYK I saw Shattered Glass when it ran in theaters and I still want my money back (http://www.autoadmit.com/thread.php?thread_id=5724617&forum_id=2...id.#48928609) |